Computer Networking concepts explained. Here’s a beginners guide to computer networking. We look at basic concepts, technologies, topologies and protocols used on home networks and the Internet.
What is an IP Address?
IP (Internet protocol) address is a numeric value that is assigned to any computer that is part of a computer network. Every machine on a network has a unique identifier so that they can communicate with each other correctly (to send/receive data).
GET INSTANT HELP FROM EXPERTS!
- Looking for any kind of help on your academic work (essay, assignment, project)?
- Want us to review, proofread or tidy up your work?
- Want a helping hand so that you can focus on the more important tasks?
Hire us as project guide/assistant. Contact us for more information
Networks nowadays (including the Internet) use the TCP/IP protocol to communicate. In the TCP/IP protocol, the unique identifier for a computer is called its IP address.
Forms of IP Address
Class A – 8 bit network prefix followed by 24 bit host number
Class B – 16 bit network prefix followed by 16 bit host number
Class C – 24 bit network prefix followed by 8 bit host number
Tracing an IP address
Reverse DNS Lookup , WHOIS , Visual Tracing Tools
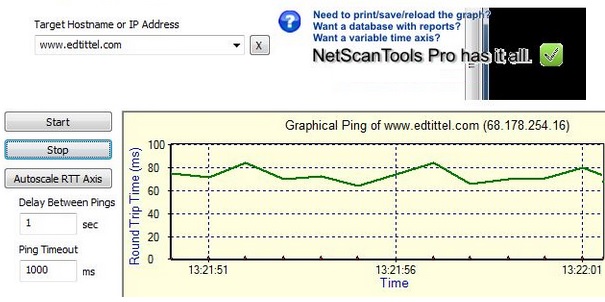
Ping
Ping calculates how long it takes to transfer a packet of information from origin [you] to destination [a web site] and back again to you.
The name comes from active sonar terminology which sends a pulse of sound and listens for the echo.
It is a computer network administration utility used to test the reachability of a host on an Internet Protocol (IP) network and to measure the round-trip time for messages sent from the originating host to a destination computer.
A Ping operates by sending Internet Control Message Protocol (ICMP) echo request packets to the target host and waiting for an ICMP response. In the process it measures the time from transmission to reception (round-trip time) and records any packet loss.
The results of the test are printed in the form of a statistical summary of the response packets received, including the minimum, maximum, and the mean round-trip times, and sometimes the standard deviation of the mean.
Depending on the implementation, the ping command can be run with various command line switches to enable special operational modes. Example options include: specifying the packet size used as the probe, automatic repeated operation for sending a specified count of probes, and time stamping.
Ping may be abused as a simple form of denial-of-service attack in the form of a ping flood, in which the attacker overwhelms the victim with ICMP echo request packets.
The increased usage of firewalls, router access lists, and other access controls means ping is not always 100 percent accurate. That is where Traceroute can be used for more accurate Network Reconnaissance.
Ping Sweep
Ping Sweep (also known as an ICMP Sweep) is a technique that can be used to find out which hosts are alive in a network or among a large number of IP addresses. Ping sweep is usually carried out for Network reconnaissance purpose! Ping stands for ‘Packet Internet Groper’!
A system administrator can detect that ping sweeping is taking place by mapping out the entire target network and pinpoint all live systems within a particular range of IP addresses.
GET INSTANT HELP FROM EXPERTS!
- Looking for any kind of help on your academic work (essay, assignment, project)?
- Want us to review, proofread or tidy up your work?
- Want a helping hand so that you can focus on the more important tasks?
Hire us as project guide/assistant. Contact us for more information
Ping Sweep tools send multiple packets at the same time and allow the user to resolve host names and save output to a file.
Tracert
Tracert is a Windows based command-line tool that helps you to determine the path taken by an Internet Protocol (IP) packet to reach a destination from a source.
It is a computer network diagnostic tool used for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network.
Traceroute is available on most operating systems.
From a system administrator’s perspective, the Tracert ICMP utility can be more effective compared to Ping. This is because the increased usage of firewalls, router access lists, and other access controls means ping is not always 100 percent accurate.
Network Reconnaissance with Traceroute, on the other hand, can be quite accurate and can be used for determining geographical information, network topography, detecting firewalls, detecting OS.
So Traceroute can be more dangerous.
Counter-measures that a system administrator can employ to counter Tracert:
- Use IP address hiding techniques
- Change Default TTL value that your OS assigns to all outgoing packets.
MAC address
MAC address is a unique value associated with the Network Adapter, also known as Physical Address. MAC address is used to uniquely identify each & every network device. MAC stands for Media Access Control address.
MAC addresses consist of 12 digit hexadecimal numbers.
The first half of a MAC address contains the ID number of the adapter’s manufacturer. The second half of a MAC address represents the serial number assigned to the adapter by the manufacturer.
MAC address is a globally unique identification and is intended to be permanent, however it is possible to change the MAC address on most modern hardware. Changing MAC addresses is necessary in network virtualization. It can also be used in the process of exploiting security vulnerabilities. This is called MAC spoofing.
Ephemeral Port
An ephemeral port is a temporary transport protocol port used for Internet Protocol (IP) communications, and is allocated automatically from a predefined range by the TCP/IP software.
An ephemeral port, also called a transient port, is set up when a client application wants to connect to a server and is destroyed when the client application terminates.
An ephemeral port is used by TCP or UDP, typically to provide the port for the client end of a client–server communication to a well-known port on a server.
On servers, ephemeral ports may also be used to continue communications with a client that initially connected to one of the server’s well-known service listening ports to make the well-known port available to service requests from other clients.
The allocations are temporary and only valid for the duration of the communication session. After completion of the communication session, the ports become available for reuse.
TCP/IP Routing Table
A routing table, also referred to as routing information base (RIB), is a data structure stored on a networked computer that lists the routes to particular network destinations, and in some cases, metrics associated with those routes.
The routing table contains information about the topology of the network immediately around it.
The information in the routing table decides what path a packet must take to travel from the source system to the destination system.
Dynamic vs. Static Routing
Routing tables may be maintained manually or dynamically. Tables for static network devices do not change unless a network administrator manually changes them. Most home routers set up their routing tables automatically when connected to the ISP (known as dynamic routing). However, business routers allow network administrators to manually update or manipulate routing tables (known as static routing) especially useful for improving network performance and reliability.
Port Scanning
TCP Connect Scanning
Pros: Fast, Accurate, Easy to Implement
Cons: Easily Detected, Traceable
TCP SYN Scanning (Half Open Scanning)
Pros: Fast, Accurate, Easy to Implement, Harder to trace than TCP Connect port-scan method
Cons: Not totally stealthy, Easily Blocked
SYN/ACK Scanning
Pros: Fast, Somewhat undetectable, Easy to Implement
Cons: Very Highly Inaccurate
One can also carry out stealth port scanning on a target system using:
TCP FIN Scanning
RCP Null Scanning
Software-Defined Networking (SDN)
Software-defined networking (SDN) is an approach to networking in which control is decoupled from hardware and given to a software application called a controller. SDN is to networking as SANs were to Data Storage, and Virtualization has been to Computers.
When a packet arrives at a switch in a conventional network, rules built into the switch’s proprietary firmware tell the switch where to forward the packet. The switch sends every packet going to the same destination along the same path — and treats all the packets the exact same way. In the enterprise, smart switches designed with application-specific integrated circuits (ASICs) are sophisticated enough to recognize different types of packets and treat them differently, but such switches can be quite expensive.
In a software-defined network, a network administrator can shape traffic from a centralized control console without having to touch individual switches. The administrator can change any network switch’s rules with a very granular level of control, which is especially helpful in a cloud computing architecture because it allows the administrator to manage traffic loads in a flexible and more efficient manner. Essentially, this allows the administrator to use less expensive, commodity switches and have more control over network traffic flow than ever before.
Keylogger
Keyylogger is basically a malicious and covert software that records all keystrokes made by the victim on a log file, which can then be sent to the attackers email-id. It can be malicious. As with most malicious software, it is also installed stealthily on the target computer.
How to prevent keyloggers from getting on to your computer:
- Never execute executable files that are sent over email, chat, IRC, etc.
- Download only from trusted sites.
What Is Checksum On Internet?
Checksum is the sum of the binary data for a given data block, in the used program. It is basically used to determine the integrity of data (to prevent data corruption and data loss).
If the data changes, its checksum value also changes.
So if the checksum value calculated by the destination program matches the checksum value calculated by the source program, then the data transfer is said to be valid and error-free.
A checksum is a string of digits (usually 128 characters) that is produced by running a file through a hash function. Calculating a checksum requires a special program (many can be downloaded for free on the Internet).
A related concept in Internet/Networking is ‘sequencing’.
All Data that is transferred over the internet is broken down into data packets at the source. These data packets then travel independently over the internet and are then joined together at the destination.
Sequencing determines the order in which the hosts should receive the data packets.
The source system breaks the data to be transferred into smaller packets and assigns a unique sequence number to each packet.
The destination needs to rearrange the packets in the right order based on the sequence number for each packet, to make the data received usable.
How to Secure DNS Servers
Domain Name System (DNS) is the primary name registration and resolution service used in Windows Server. DNS provides a hierarchically distributed and scalable database; provides name registration and name resolution services, and service location for Windows clients; and locates domain controllers for logon.
It’s important to ensure that your DNS infrastructure is protected from attack from outside—or even inside—your organization. There are various ways in which you can configure your DNS server to prevent unauthorized modifications to DNS data. You can take additional steps to reduce the chances of an attacker being able to compromise the integrity of your DNS infrastructure.
Here are steps that you can take to secure DNS Servers:
- Use DNS forwarders
- Use caching-only DNS servers
- Use DNS advertisers
- Use DNS resolvers
- Protect DNS from cache pollution
- Enable DDNS for secure connections only
- Disable zone transfers
- Use firewalls to control DNS access
- Set access controls on DNS registry entries
- Set access control on DNS file system entries
Proxy Server vs Proxy Bouncing
If you connect to the internet via a server, all your content is basically served on your behalf by that server, which is known as the ‘proxy server’. So, if several computers connect to internet via a proxy server, the proxy server will be the only real computer downloading all the content and in turn serve it to the clients.
What are the advantages of proxy bouncing compared with proxy servers?
In proxy bouncing, the user bounces of several different proxy servers before connecting to the actual destination system. Proxy bouncing makes it difficult to trace the computer of the user.
How to carry out proxy bouncing?
Proxy server tools are available that will not only allow you to connect to several different proxy servers, but they also have the ability to keep changing the proxy servers periodically.
Network Sniffers
Network Sniffers are recording software that record and store (and analyze) data packets that are sent across the network. These are installed stealthily on the target computer and can be used in a malicious manner. Companies should switch to switching networks and use encryption, to ensure adequate protection.
These help in debugging network problems and are also used as spying tools. They capture and interpret packets sent across a network for analysis purpose. Network sniffers also help system administrators to debug or troubleshoot network problems.
For example, you will be able to see what websites your child is visiting, and even sniff out their passwords to their email too!
Sniffers can be used to discover some serious loopholes in our networks. It is easy to use a network sniffer in an easy, repeatable process to find unusual, unauthorized and just plain insecure protocols on our networks quickly and easily.
These are also referred to as ‘Network Monitor’.
Sniffers are tools for debugging network problems. It is also used as a spying tool. They capture and interpret packets sent across a network for analysis purpose.
It can also help system administrators to debug or troubleshoot network problems.
Here are the important features:
- They are Stealthy as they don’t generate any network traffic, and therefore are hard to detect
- They work on any workstation, and don’t require any additional software on the target PCs
- At the more advanced level, they can analyze raw packets, and extract application protocol information
Popular Network Monitors include:
- TCP/IP Packet Sniffer: Connection-Oriented Sniffer and Protocol Analyzer.
- HTTP Sniffer: Informs you Who have surfed online and where.
- Password Sniffer: Capture passwords through http, ftp, smtp, pop3, telnet.
- MSN Sniffer: Monitor MSN messenger conversation on network!
Active Fingerprinting vs Passive Fingerprinting
These are techniques used for operating system detection. Different operating systems respond differently to certain type of packets. Both these techniques study the responses.
- Active fingerprinting reveals the attackers identity to the target system.
- Passive fingerprinting enables the attackers to anonymously determine the operating system running on the target host.
The ‘Passive Fingerprinting’ information gathering technique is better from the attacker’s perspective because it lets the attacker anonymously detect the Operating System (OS). Once the OS is known, the attacker can find more about ports, processes, and services running on that computer, and of any potential loopholes.
Passive fingerprinting involves using a sniffer to passively analyze data sent by the target system regardless of their contents or intended destination.
- The sniffer is not installed on the attackers system but on a system that is sure to receive data sent by the target system.
- It could be on the router of the target systems network or on any system that regularly communicates with the target system. TTL value, window size, DF bit, TOS are the four values (part of the captured data packets) that are then studied.
So what counter-measures can be taken to prevent fingerprinting probes?
Here are some:
- Change the default TTL value that the operating system assigns to all outgoing packets.
- Change the default values that the OS assigns to various fields of a packet.
- Use ACL to filter-out unwanted packet
GET INSTANT HELP FROM EXPERTS!
- Looking for any kind of help on your academic work (essay, assignment, project)?
- Want us to review, proofread or tidy up your work?
- Want a helping hand so that you can focus on the more important tasks?
StudyMumbai.com is an educational resource for students, parents, and teachers, with special focus on Mumbai. Our staff includes educators with several years of experience. Our mission is to simplify learning and to provide free education. Read more about us.

Leave a Reply
You must be logged in to post a comment.